Featured
Table of Contents
- – Different Types Of Vpn Protocols (Tunnels) & ...
- – Guide To Vpn Protocols: Using Vpns Securely In...
- – What Is A Vpn Tunnel And How Does It Work?
- – What Is A Vpn Tunnel? An Easy Guide
- – Vpn Protocols: Are You Using The Right One?
- – Vpn Protocols – 9 Most Popular Protocols Exp...
- – Definition, How It Works, And Protocols Used...
- – What Is Vpn Encryption And How Does It Work?
- – What Is A Vpn Tunnel And How It Works - Xvpn
- – What's The Difference Between Tunneling And ...
Different Types Of Vpn Protocols (Tunnels) & ...
The strength of a tunnel depends upon the kind of tunneling protocol your VPN supplier utilizes. Some procedures are dated and might not supply information encryption that is strong enough to hinder online snoops so it's an excellent idea for you to deal with a VPN service provider that counts on the strongest possible tunneling protocol.
That locks out numerous possible users. If you're looking for the greatest security while online, you must think about buying a VPN provider that relies on the Open, VPN procedure. This procedure works with all the major os, Linux, Window, and Mac, on the mobile os of Android and i, OS.
Guide To Vpn Protocols: Using Vpns Securely In 2023
His work has actually appeared in the Washington Post, Chicago Tribune, and Fox Organization. Our offerings might not cover or safeguard versus every type of criminal offense, scams, or danger we write about.
Please review total Terms during enrollment or setup. Keep in mind that no one can prevent all identity theft or cybercrime, which Life, Lock does not keep track of all transactions at all businesses. The Norton and Life, Lock brands belong to Gen Digital Inc.
What Is A Vpn Tunnel And How Does It Work?
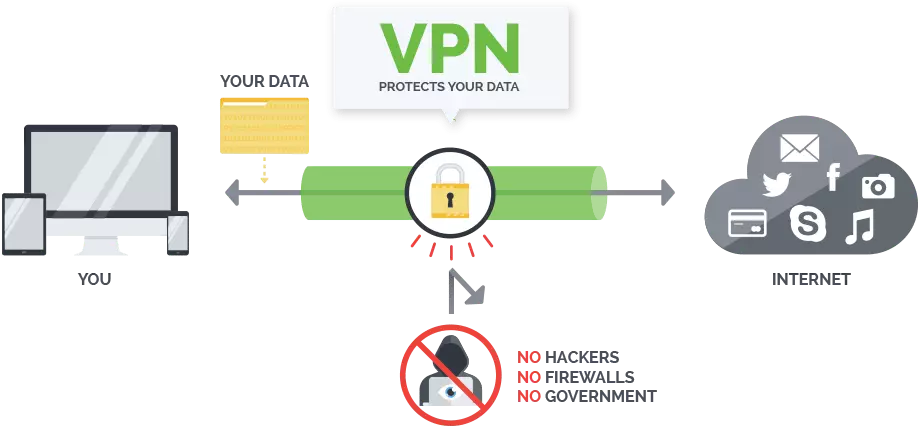
The simple VPN has actually ended up being progressively popular in recent years, primarily since they have the ability to bypass government censorship and geo-blocked websites and services. Much better still, a trusted VPN will allow you to do this without distributing who is doing the bypassing. In order for a VPN to do this, it creates what is called a tunnel between you and the web.
When you link to the web with a VPN, it develops a connection in between you and the web that surrounds your internet data like a tunnel, securing the information packages your gadget sends out. While technically produced by a VPN, the tunnel on its own can't be considered personal unless it's accompanied with encryption strong enough to avoid federal governments or ISPs from obstructing and reading your internet activity.
What Is A Vpn Tunnel? An Easy Guide
Let's take a better look at them.
As a Windows-based tunneling procedure, SSTP is not available on any other operating system, and hasn't been individually examined for potential backdoors developed into the protocol. Conserving the very best for last, we have Open, VPN, a relatively current open source tunneling protocol that utilizes AES 256-bit encryption to secure information packets.
Vpn Protocols: Are You Using The Right One?
A good VPN service must use you the option of a minimum of these 4 kinds of tunneling procedures when going online. When it comes to the very best VPN to sign up for there are a lot of alternatives to pick from. Of course, if money is tight and you're not too keen on investing anything more than you have to, trying the very best low-cost VPN might be an alternative.
The main problem with selecting a totally free VPN is that you normally will not get the very same worth as that offered by a paid-for competitor. What's more, if you're utilizing a VPN then among the primary considerations is going to revolve around security. By picking a less widely known VPN, rather than the major gamers such as Express, VPN, Nord, VPN, Surfshark or IPVanish to call but 4, you might not get the same level of defense.
Vpn Protocols – 9 Most Popular Protocols Explained
Free VPNs can be a little parsimonious when it pertains to the quantity of information you can utilize, with the operating speed often being less remarkable than paid-for alternatives too. If you've got a desire to stream video or are torrenting on a regular basis, this may be incorrect economy.
A low-cost VPN company will frequently have much of the very same functions and functions discovered in those superior editions, however you'll make some cost savings too.We've noted the very best company VPN. Tech, Radar Pro developed this material as part of a paid collaboration with Express, VPN. The contents of this post are completely independent and solely reflect the editorial opinion of Tech, Radar Pro.
Definition, How It Works, And Protocols Used By Vpns
While it's challenging to establish by itself, Open, VPN is great for speed, security, and file encryption. Express, VPN users can toggle between UDP (optimum for speed) or TCP (optimum for connection reliability.)Among the more recent VPN procedures available to customers, IKEv2 is considered to be a lighter and more steady choice than Open, VPN.
Due to its absence of file encryption and authentication features, PPTP is the fastest VPN procedure. This implies that your internet traffic can be seen by third celebrations. We do not recommend using PPTP, and it is no longer supported on Express, VPN apps.
What Is Vpn Encryption And How Does It Work?
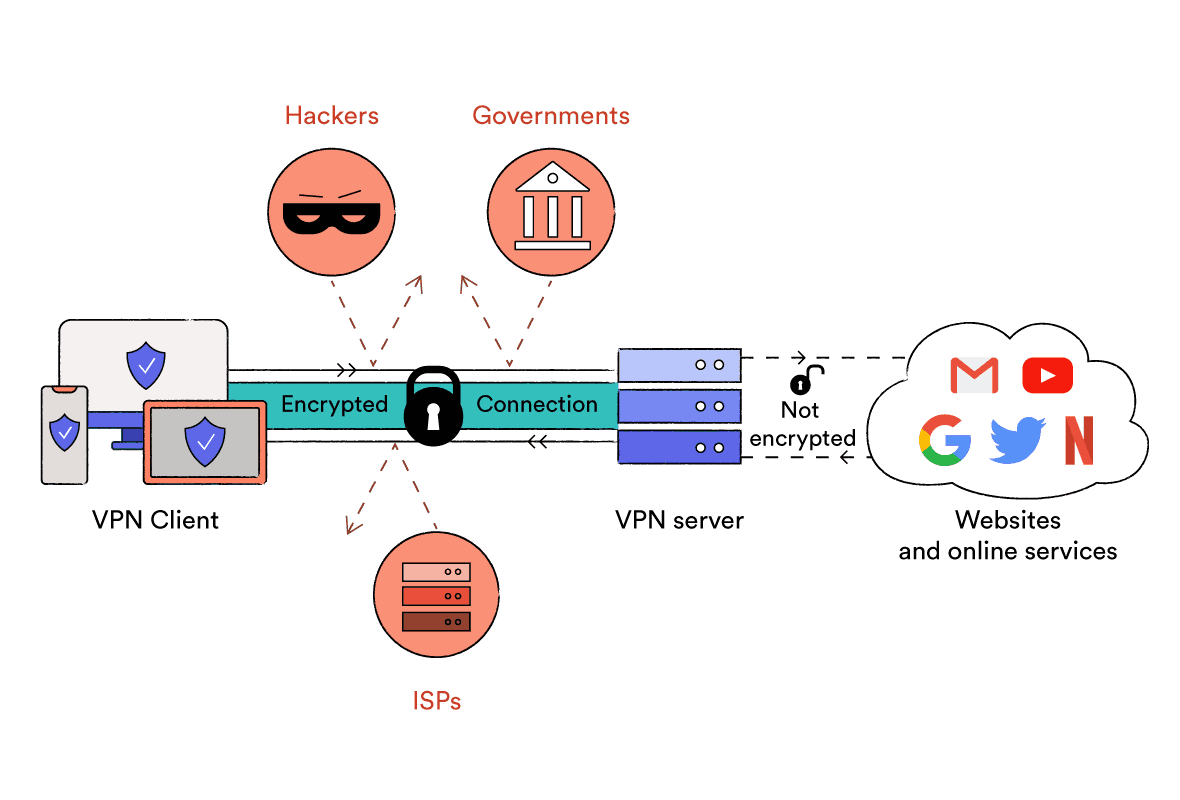
Table of contents It's just plain scary to think about, isn't it? But the sad fact is, this is simply how your connection to the web works it resembles an open window into the goings on in your house, and any nosey parker can peep through. Whether it's your Internet Service Service Provider (ISP) looking to track and sell your data to marketers, or dishonest hackers trying to steal your personal information to sell on the dark web, it in some cases seems like the entire world has a beneficial interest in sleuthing on your online activity.
There are a number of methods to ward off potential online snoopers, one of which includes using a Virtual Private Network (VPN). In a nutshell, VPNs assist you browse the web safely, privately, and without any constraints. (We've already waxed lyrical on the advantages of using a VPN before, so we will not harp on again excessive here).
What Is A Vpn Tunnel And How It Works - Xvpn
Hey, dropped connections take place sometimes, even to the extremely best (and most costly) VPNs. This is why most credible VPN suppliers come with a seriously useful feature an automatic kill switch.
Tunneling uses a layered protocol model such as those of the OSI or TCP/IP protocol suite, but generally breaches the layering when using the payload to carry a service not generally offered by the network. Usually, the shipment procedure operates at an equal or greater level in the layered design than the payload procedure.
What's The Difference Between Tunneling And Vpn?
The proxy then makes a TCP connection to a particular server: port, and relays data between that server: port and the client connection. Because this produces a security hole, CONNECT-capable HTTP proxies commonly limit access to the CONNECT approach.
Even though the SMB protocol itself contains no file encryption, the encrypted SSH channel through which it travels deals security. Local and remote port forwarding with ssh carried out on the blue computer system. Once an SSH connection has been established, the tunnel begins with SSH listening to a port on the remote or local host.
Table of Contents
- – Different Types Of Vpn Protocols (Tunnels) & ...
- – Guide To Vpn Protocols: Using Vpns Securely In...
- – What Is A Vpn Tunnel And How Does It Work?
- – What Is A Vpn Tunnel? An Easy Guide
- – Vpn Protocols: Are You Using The Right One?
- – Vpn Protocols – 9 Most Popular Protocols Exp...
- – Definition, How It Works, And Protocols Used...
- – What Is Vpn Encryption And How Does It Work?
- – What Is A Vpn Tunnel And How It Works - Xvpn
- – What's The Difference Between Tunneling And ...
Latest Posts
Get The Best Business Vpn 2023 - Expressvpn
The 5 Best Vpn Services For The Bay Area
Best Vpns For China In 2023 (+ My Strategy To Use Them)
More
Latest Posts
Get The Best Business Vpn 2023 - Expressvpn
The 5 Best Vpn Services For The Bay Area
Best Vpns For China In 2023 (+ My Strategy To Use Them)